Research
Security baselines
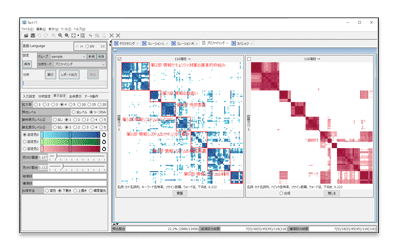
In this research, we are developing a document analysis tool, Tact, by combining clustering techniques (hierarchical clustering), natural language processing, topic modeling, and many other statistical analysis techniques. The document analysis tool Tact can be used for comparative analysis of documents, analysis of document structure, evaluation of document maturity and deterioration, and analysis of keyword distribution in documents. …
Anomaly detection
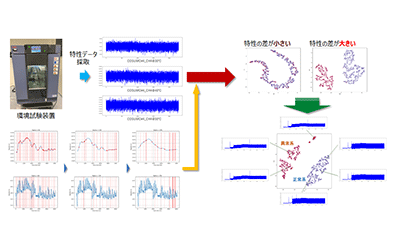
A seemingly meaningless stream of data, such as the current flowing through an electronic circuit or the information flow through a network, contains a large amount of information. In this research, we are developing a waveform analysis tool @blewm (pronounced, abloom) by combining component analysis technology, data expansion technology, reinforcement learning, and clustering techniques (spectral clustering). …

Electronic device protection
In this research, we have developed a security device SS-AID by combining retrofit processing, board design, circuit design, and environmental resistance evaluation technologies that do not assume high capital investment or advanced processing technology. …
Researcher

Hitoshi Osaki
Team Leader. After working as a researcher at AIST (2000), he is currently the head of the Infrastructure Protection Security Research Team at the Cyber Physical Security Research Institute of AIST. He has a background in overseas research at the University of Illinois in the United States (2007-2008), secondment to the Ministry of Economy, Trade and Industry (2013-2014), and concurrently serving as a security trade management researcher at the Ministry of Economy, Trade and Industry (2018-2020). Specializes in computational theory. Received the Young Scientist Award from the Minister of Education, Culture, Sports, Science and Technology (2006).

Akihisa Yamada
Received a Ph.D. in information science from Nagoya University in 2014. Currently, he is a senior researcher in the Infrastructure Protection Security Research Team, Cyber Physical Security Research Institute, AIST. Specializes in term rewriting and formal logic.

Norihisa Yuki
Collaborating Visitor (National center of Incident readiness and Strategy for Cybersecurity)

Hiroyuki Seki
Invited Researcher(Nagoya Univ.)

Kenichi Handa
Invited Researcher

Isao Tatsuno
Collaborating Visitor (FUKKO SYSTEM CO., LTD.)

CHANGKYU KIM
Collaborative Researcher(TRIAN LLC)
