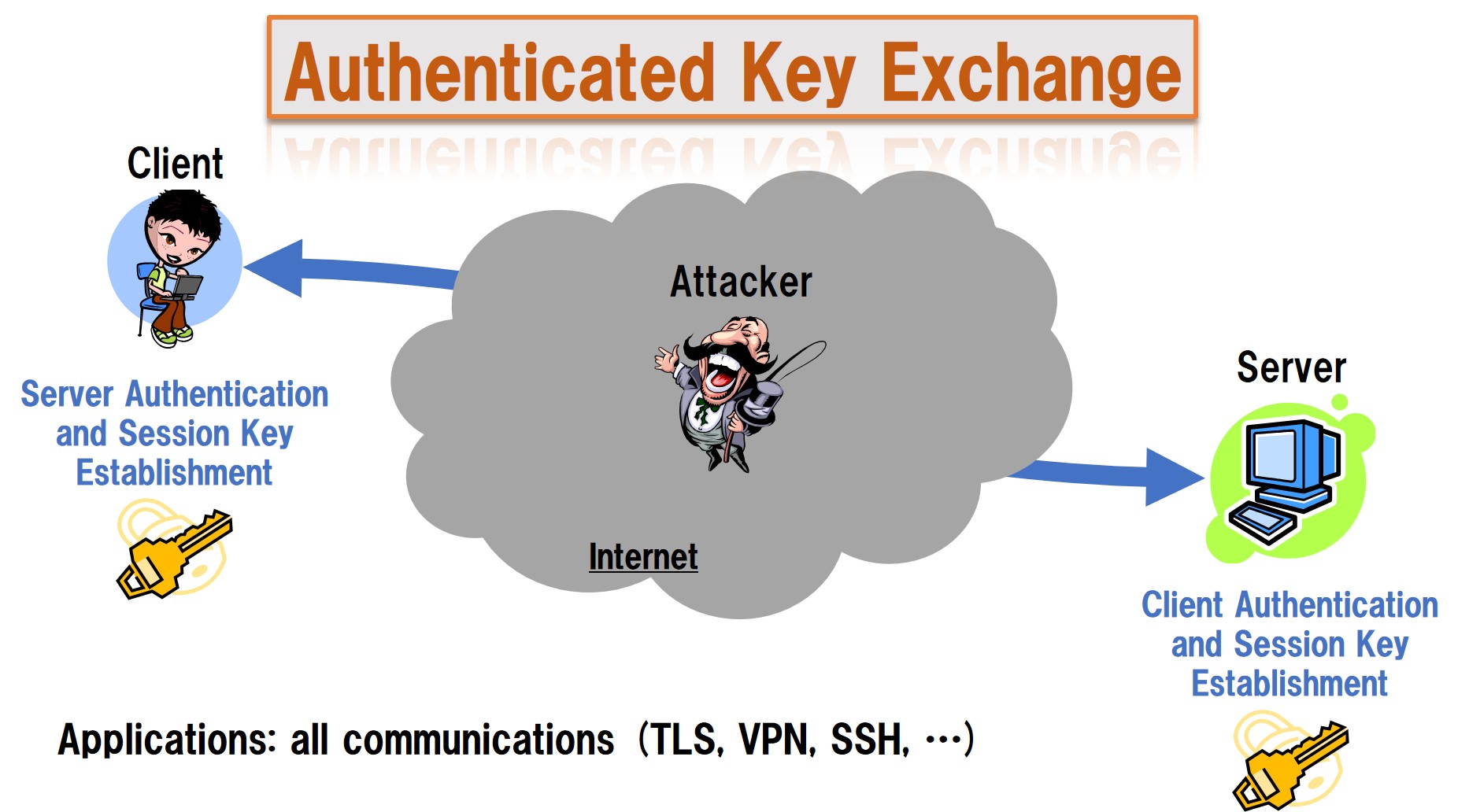
Cryptographic Authentication and Key Exchange
Entity authentication and key exchange are indispensable cryptographic technologies for all communications, including IoT/CPS. Among them, Authenticated Key Exchange (AKE) protocols allow each entity to authenticate corresponding parties through public networks such as the Internet and share session keys to establish secure channels. These protocols have already been widely used in the real world, such as HTTPS, VPN, TLS, and SSH.
Currently, we are conducting research and development on cryptographic technologies such as entity authentication and key exchange (key management) not only for security and efficiency but also for various use cases and applications and are promoting international standardization.
Research Result
- SeongHan Shin, “Leakage-Resilient and Proactive Authenticated Key Exchange (LRP-AKE), Reconsidered,” IEICE Transactions on Information and Systems (To appear)
- ISO/IEC 11770-4:2017/Amd 2:2021 (International Standard)
- SeongHan Shin, “Authenticated Key Exchange from Weak Secrets,” Tutorial Talk, WISA 2020
- SeongHan Shin, Shota Yamada, Goichiro Hanaoka, Yusuke Ishida, Atsushi Kunii, Junichi Oketani, Shimpei Kunii, and Kiyoshi Tomomura, “An Extended CTRT for AES-256,” WISA 2019, LNCS 11897, pp. 79-91, 2019 (WISA 2019 Best Paper Premium Award)
- SeongHan Shin and Kazukuni Kobara, “How to Preserve User Anonymity in Password-Based Anonymous Authentication Scheme,” IEICE Transactions on Information and Systems, Vol. E101-D, No. 3, pp. 803-807, 2018
- ISO/IEC 11770-4:2017-11 (International Standard)
- ISO/IEC 20009-4:2017-08 (International Standard)
- SeongHan Shin and Kazukuni Kobara, “Security Analysis of Password-Authenticated Key Retrieval,” IEEE Transactions on Dependable and Secure Computing, Vol. 14, No. 5, pp. 573-576, 2017
- SeongHan Shin and Kazukuni Kobara, “Simple Anonymous Password-Based Authenticated Key Exchange (SAPAKE), Reconsidered,” IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, Vol. E100-A, No. 2, pp. 639-652, 2017
- SeongHan Shin, Kazukuni Kobara, Chia-Chuan Chuang, and Weicheng Huang, “A Security Framework for MQTT,” IEEE International Workshop on Cyber-Physical Systems Security, 2016
- SeongHan Shin, Kazukuni Kobara, and Hideki Imai, “On Finding Secure Domain Parameters Resistant to Cheon's Algorithm,” IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, Vol. E98-A, No. 12, pp. 2456-2470, 2015
- SeongHan Shin and Kazukuni Kobara, “On Unlinkability of Password-Based Anonymous Authentication,” IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, Vol. E98-A, No. 6, pp. 1320-1324, 2015