Research on evaluation techniques for detecting LSI vulnerabilities
In today's information society, not only information terminals such as smart phones and computers, but also cars, machine tools in factories, and many other things are electrically controlled. There is a growing concern about the risk of leakage of confidential information and malfunction of these electronic devices due to intrusion from external networks or contamination by malwares. The "strength" of many securities and cryptographic functions depends on the hardware (LSI chip) of the electronic devices, and it is important to evaluate whether the LSI chip is sufficiently secure or not.
Side-channel attacks are known to be one of the most serious threats to LSI chips.
It has been shown that some cryptographic systems can be broken by side-channel attacks, which use supplemental information such as power consumption leaked from the electronic devices to infer the internal state of the devices. Due to the existence of side-channel attacks, it is necessary not only to prove whether the cryptographic systems are theoretically secure or not, but also to evaluate whether the information is leaked to the power consumption of each LSI chip after the cryptographic systems are implemented in the LSI chips.
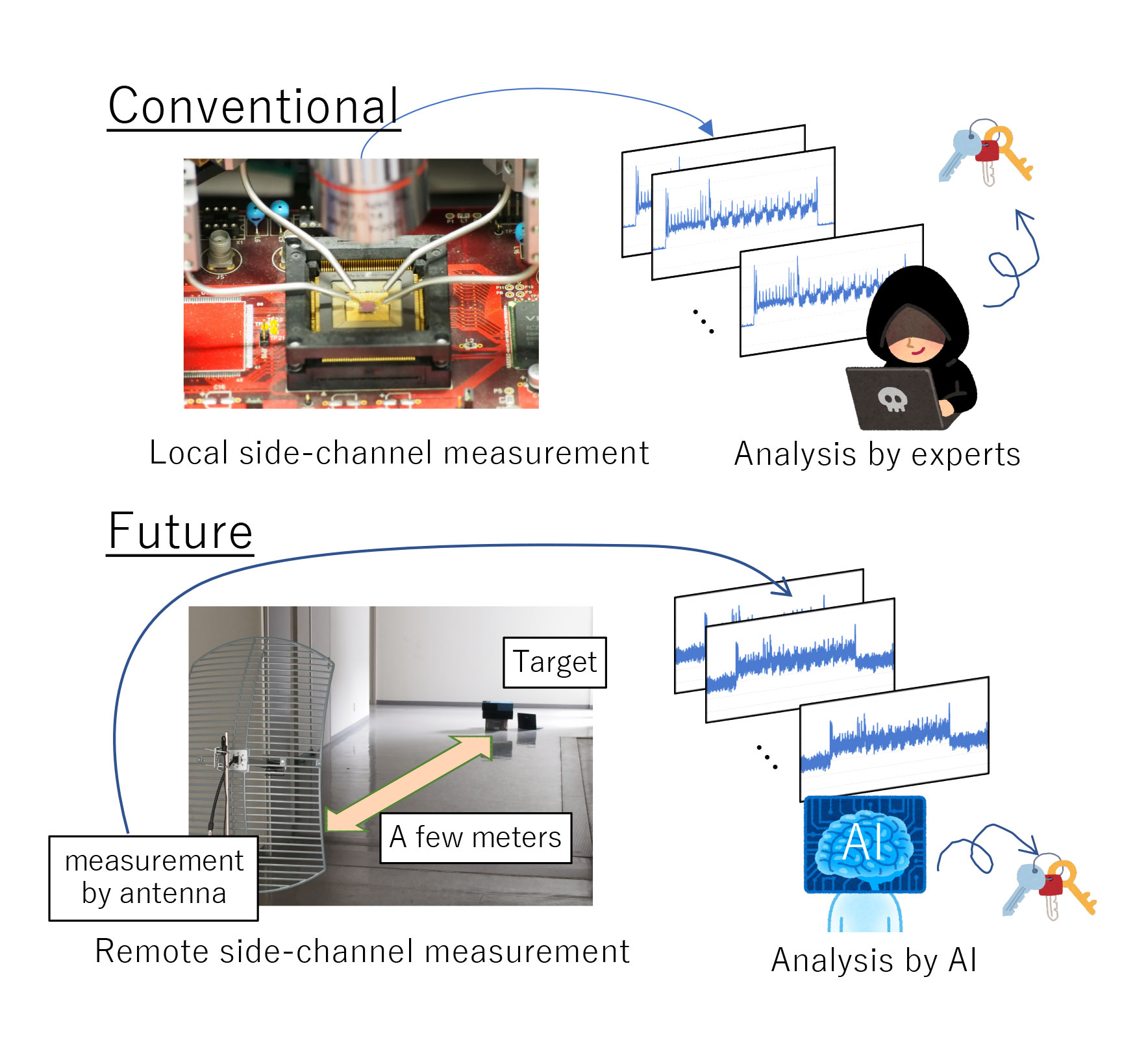
Conventional side-channel attacks have been thought to require the attackers to be in close proximity to the device to obtain information such as power consumption, but recent research has shown that for devices such as wireless devices, power consumption can be mixed with wireless radio waves to reach distant locations, making attacks possible from a distance. In addition, with the progress of machine learning techniques such as deep learning, applying machine learning to key recovery in side-channel attacks has been proposed. In the past, side-channel attacks could only be successfully carried out by a certain type of specialist who properly set the parameters, but there are concerns that anyone can easily carry out such attacks by using machine learning. To counter such sophisticated attacks, we are researching techniques to evaluate whether a device can be attacked or not before it is released to the public. We have one of the best facilities and human resources in Japan to tackle this problem, and we are constantly preparing the environment for the latest vulnerability assessments and developing countermeasure techniques to prevent vulnerabilities from entering the system.
Reference
- Yusuke Yano, Kengo Iokibe, Toshiaki Teshima, Yoshitaka Toyota, Toshihiro Katashita, Yohei Hori, "Evaluation of Side-Channel Leakage Simulation by Using EMC Macro-Model of Cryptographic Devices," IEICE Transactions on Communications, Vol. E104.B, No. 2, pp.178-186, Feb., 2021. DOI: 10.1587/transcom.2020EBP3015
- Daisuke Fujimoto, Noriyuki Miura, Makoto Nagata, Yuichi Hayashi, Naofumi Homma, Takafumi Aoki, Yohei Hori, Toshihiro Katashita, Kazuo Sakiyama, Thanh-Ha Le, Julien Bringer, Pirouz Bazargan-Sabet, Shivam Bhasin, Jean-Luc Danger, "Power Noise Measurements of Cryptographic VLSI Circuits Regarding Side-Channel Information Leakage," IEICE Transactions on Electronics, Vol.E95-C, pp.272-279, Apr., 2014.
- Takeshi Fujino, Daisuke Suzuki, Yohei Hori, Mitsuru Shiozaki, Masaya Yoshikawa, Toshiya Asai, Masayoshi Yoshimura, "Malicious Attacks on Electronic Systems and VLSIs for Security," in Shojiro Asai (Ed.), "VLSI Design and Test for Systems Dependability", Chap.10, pp.395-437, 2019. (eBook 2018)
- J. Sakamoto, S. Hayashi, D. Fujimoto, and T. Matsumoto. “Constructing Software Countermeasures Against Instruction Manipulation Attacks: An Approach Based on Vulnerability Evaluation Using Fault Simulator,” Cluster Computing Journal, Springer. To appear.
- S. Kawamura, Y. Komano, H. Shimizu, S. Osuka, D. Fujimoto, Y. Hayashi, K. Imafuku, “Efficient algorithms for sign detection in RNS using approximate reciprocals,” IEICE Trans. Vol.E104-A, No.1, (Jan. 2021).