Security Analysis and High-Speed Implementation of Cryptographic Primitives and Protocols
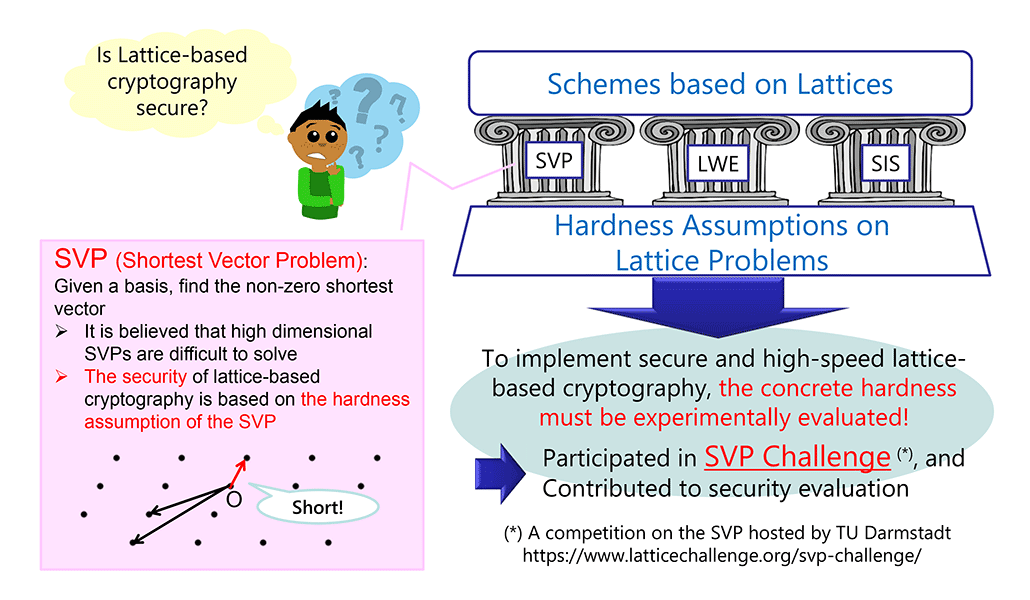
Even if the security of cryptographic and secure computation protocols is theoretically proven, it does not immediately follow that those protocols can be used with confidence. For example, in lattice-based cryptography, it is necessary to evaluate the concrete hardness of the lattice problem on which the security is based. Also, the security model may not capture the real threats. Furthermore, it is difficult to properly implement and use cryptographic protocols, and security can be lost for various reasons, such as the implementation, usage, and mistakes. To overcome these problems and enable the development of secure, high-speed, and practical cryptographic protocols, our research team conducts study on evaluating the security of cryptographic protocols, reconsidering the underlying security models, and developing faster algorithms and implementation techniques.
Paper List
- Tadanori Teruya: A Note on Subgroup Security in Discrete Logarithm-Based Cryptography, IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, Vol.E104-A(1), pp.104-120, (2021)
- Tadanori Teruya: Security analysis of elliptic curves with embedding degree 1 proposed in PLOS ONE 2016, PLOS ONE, Vol.14(2), pp.1-11 (2019)
- Yoshitatsu Matsuda, Tadanori Teruya, Kenji Kashiwabara: Efficient Estimation of Number of Short Lattice Vectors in Search Space under Randomness Assumption, Proceedings of the 6th ACM ASIA Public-Key Cryptography Workshop (APKC), pp.13-22, (2019)
- Nuttapong Attrapadung, Goichiro Hanaoka, Shigeo Mitsunari, Yusuke Sakai, Kana Shimizu, Tadanori Teruya. Efficient Two-level Homomorphic Encryption in Prime-order Bilinear Groups and A Fast Implementation in WebAssembly. In Proceedings of the 13th ACM ASIA Conference on Information, Computer and Communications Security (ACM ASIACCS), pp.685-697 (2018)
- Tadanori Teruya, Kenji Kashiwabara, Goichiro Hanaoka: Fast Lattice Basis Reduction Suitable for Massive Parallelization and Its Application to the Shortest Vector Problem, Proceedings of the 21st IACR International Conference on Practice and Theory of Public-Key Cryptography (PKC), Lecture Notes in Computer Science, Vol.10769, pp.437-460, (2018) and Theory of Public-Key Cryptography (PKC), Lecture Notes in Computer Science, Vol.10769, pp.437-460, (2018)