Privacy Preserving Technologies for Data Analysis and Machine Learning
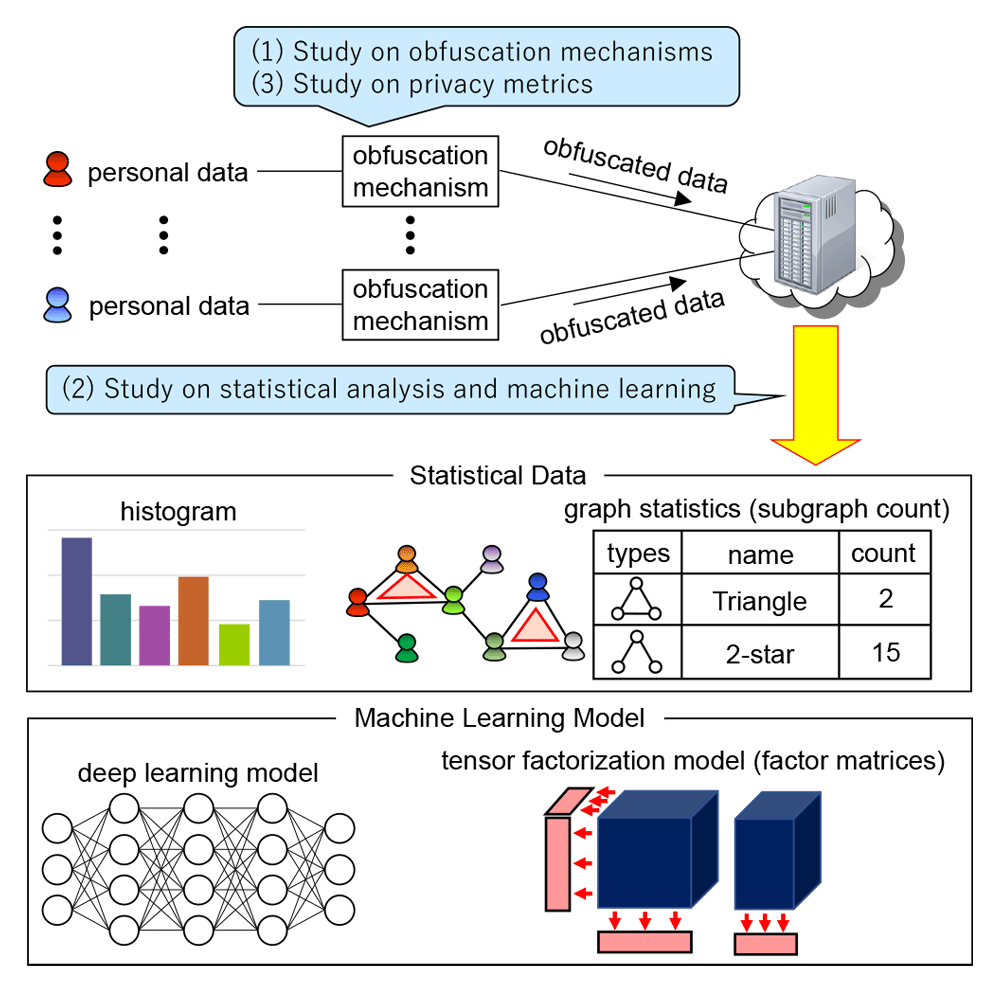
With the widespread use of IoT (Internet of Things), mobile devices, and social networks, we are facing a need for performing statistical analysis while protecting user privacy. For example, we can calculate a histogram from users’ personal data (e.g., locations, electric power consumption) to analyze popular sightseeing places or power usage patterns. For another example, we can count subgraphs such as triangles and k-stars (one node connected to k other nodes) from a social graph to calculate the probability that two friends of a user will also be a friend (=3 #triangles / #2-stars). Since these statistical data might reveal sensitive information (e.g., home, life patterns, friendship), we need to perform these tasks while protecting user privacy. Moreover, with the rapid development of AI (Artificial Intelligence), we are also facing a need for building machine learning models (e.g., deep learning, SVM, matrix/tensor factorization) while protecting user privacy.
To achieve this, our research team is working on the following three topics: (1) algorithms that obfuscate personal data so that it satisfies strong privacy metrics such as differential privacy; (2) algorithms that perform statistical analysis or build machine learning models for the obfuscated data; (3) new privacy metrics that balance high privacy and utility. For example, differential privacy is known as a gold standard for data privacy because it protects user privacy against adversaries with any background knowledge. In (1) and (2), we aim to perform statistical analysis or build machine learning models while providing such a strong privacy metric.
For some applications, it is unclear to what extent private information will be leaked if personal data are not obfuscated. Conversely, it is also unclear to what extent data utility will be lost if we use a privacy metric that requires too strong privacy. In (3), we tackle these open questions and establish a new privacy metric that provides both high privacy and utility.
Paper List
- Jacob Imola*, Takao Murakami*, Kamalika Chaudhuri (*: equal contribution), "Locally Differentially Private Analysis of Graph Statistics," Proceedings of the 30th USENIX Security Symposium (USENIX Security 2021), pp.983-1000, 2021.
- Seira Hidano, Takao Murakami, Yusuke Kawamoto, "TransMIA: Membership Inference Attacks Using Transfer Shadow Training," Proceedings of the 2021 International Joint Conference on Neural Networks (IJCNN 2021), 2021 (to appear).
- Takao Murakami, Koki Hamada, Yusuke Kawamoto, Takuma Hatano, "Privacy-Preserving Multiple Tensor Factorization for Synthesizing Large-Scale Location Traces with Cluster-Specific Features," Proceedings on Privacy Enhancing Technologies (PoPETs), Issue 2, pp.5-26, 2021.
- Seira Hidano, Takao Murakami, Shuichi Katsumata, Shinsaku Kiyomoto, Goichiro Hanaoka, "Exposing Private User Behaviors of Collaborative Filtering via Model Inversion Techniques," Proceedings on Privacy Enhancing Technologies (PoPETs), Issue 3, pp.264-283, 2020.
- Yusuke Kawamoto, Takao Murakami, "Local Distribution Obfuscation via Probability Coupling," Proceedings of the 57th Annual Allerton Conference on Communication, Control, and Computing (Allerton 2019), pp.718-725, 2019.
- Yusuke Kawamoto, Takao Murakami, "Local Obfuscation Mechanisms for Hiding Probability Distributions," Proceedings of the 24th European Symposium on Research in Computer Security (ESORICS 2019), pp.128-148, 2019.
- Takao Murakami, Yusuke Kawamoto, "Utility-Optimized Local Differential Privacy Mechanisms for Distribution Estimation," Proceedings of the 28th USENIX Security Symposium (USENIX Security 2019), pp.1877-1894, 2019.
- Seira Hidano, Takao Murakami, Shuichi Katsumata, Shinsaku Kiyomoto, Goichiro Hanaoka, "Model Inversion Attacks for Online Prediction Systems: Without Knowledge of Non-Sensitive Attributes," IEICE Transactions on Information and Systems, Vol.101-D, No.11, pp.2665-2676, 2018.
- Takao Murakami, Hideitsu Hino, Jun Sakuma, "Toward Distribution Estimation under Local Differential Privacy with Small Samples," Proceedings on Privacy Enhancing Technologies (PoPETs), Issue 3, pp.84-104, 2018.
- Takao Murakami, "Expectation-Maximization Tensor Factorization for Practical Location Privacy Attacks," Proceedings on Privacy Enhancing Technologies (PoPETs), Issue 4, pp.138-155, 2017.
- Takao Murakami, Atsunori Kanemura, Hideitsu Hino, "Group Sparsity Tensor Factorization for Re-identification of Open Mobility Traces," IEEE Transactions on Information Forensics and Security, Vol.12, No.3, pp.689-704, 2017.
- Seira Hidano, Takao Murakami, Shuichi Katsumata, Shinsaku Kiyomoto, Goichiro Hanaoka, "Model Inversion Attacks for Prediction Systems: Without Knowledge of Non-Sensitive Attributes," Proceedings of the 15th International Conference on Privacy, Security, and Trust (PST 2017), pp.115-126, 2017.
- Takao Murakami, Hajime Watanabe, "Localization Attacks Using Matrix and Tensor Factorization," IEEE Transactions on Information Forensics and Security, Vol.11, No.8, pp.1647-1660, 2016.
- Takao Murakami, Atsunori Kanemura, Hideitsu Hino, "Group Sparsity Tensor Factorization for De-anonymization of Mobility Traces," Proceedings of the 14th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom 2015), pp.621-629, 2015. [Best Paper Award]