Privacy-Preserving Information Analysis
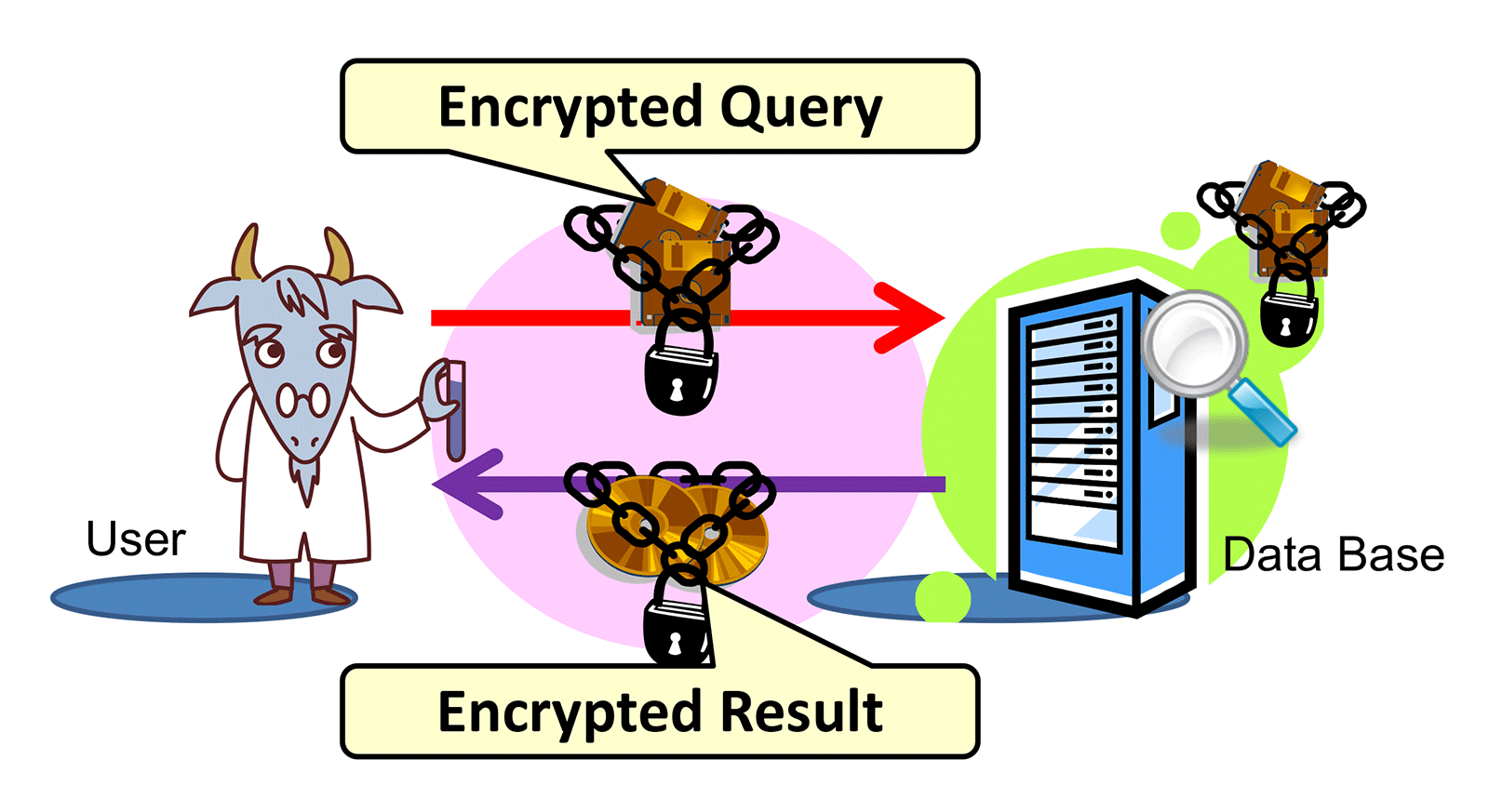
In this information age, many individuals and organizations generate plenty of information and such information is organized as databases. Inter-database analysis over such databases can help us to progress science and technology and improve a social system.
Such databases are, however, quite private, since they are related to individuals' privacy or organizations' business secrets. The individuals and organizations do not want to provide such information to an inter-database analysis. Our research team studies "multiparty computation", which enables us to analyze databased while keeping the database contents private as much as possible.
A simple example is: Two shops organize a tied-up sale, in which they want to send an announcement to the customers who are common to their customer lists. The shops simultaneously do not want to disclose the information on the customers who are not common between the lists. Using multiparty computation, the shops can obtain the common customers in the lists, while keeping the rest of the lists private to each other.
Another example is analyzing a biomedical database of intractable disease patients to find a factor that is tightly related to the disease in such a way that the patients' privacy is preserved. Our research team studies highly functional, efficient, and secure multiparty computation to enable the above useful applications.
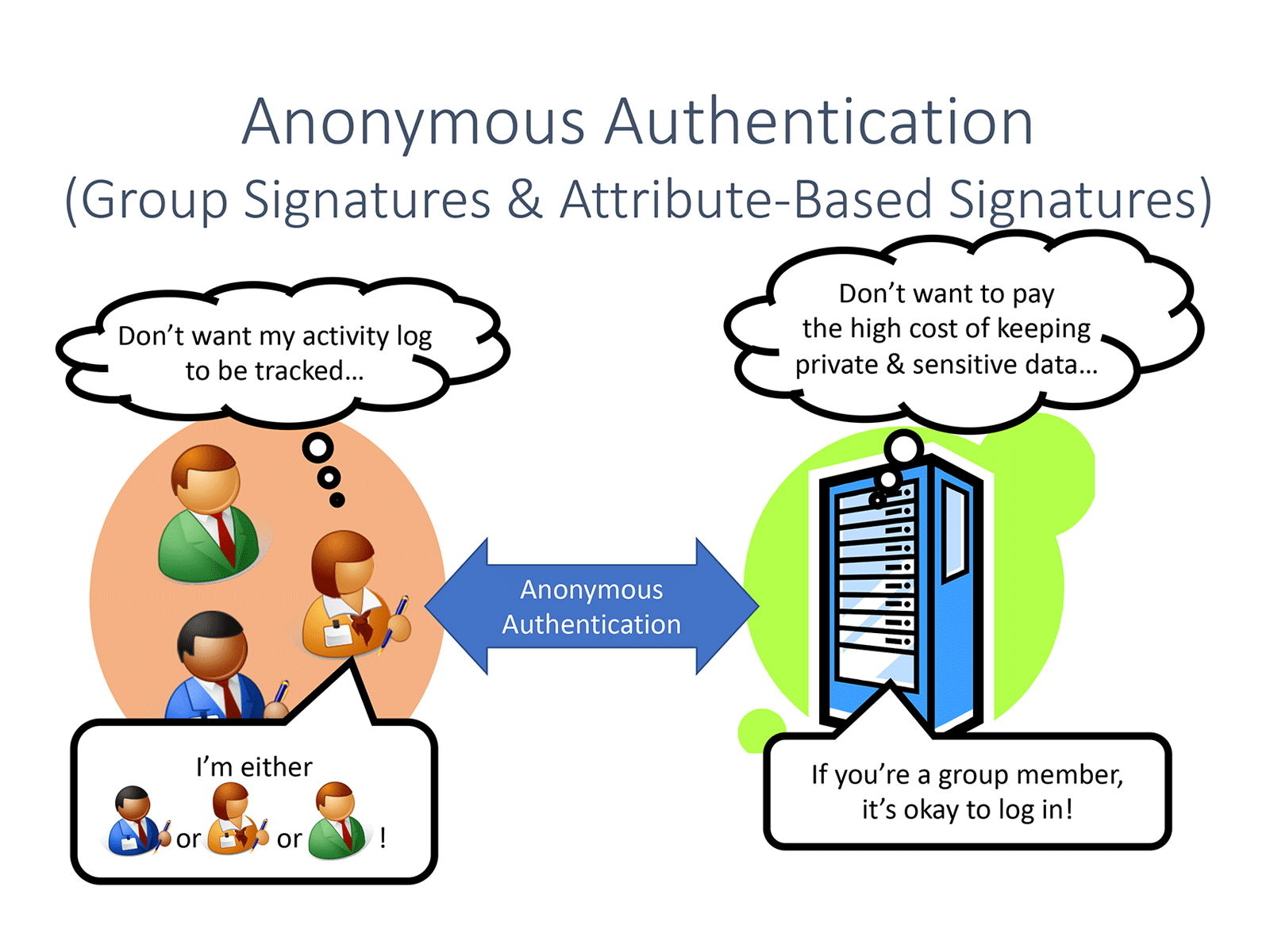
Often, it is useful to analyze customers' online activities for improving an online service. To obtain a trustworthy activity log of customers, it is essential to authenticate customers. Authentication is of course crucial if the service is provided for members. In addition, it is also important if the service provider wants to distinguish different users for having different logs for different users.
Nonetheless, online activities are highly sensitive and private information. Then users and the service provider want to restrict the information that the service provider gathers to the smallest amount. This is because users want to reduce the risk of privacy invasion and the service provider wants to reduce the management cost of such sensitive information.
Anonymous authentication fulfills these needs. Using group signatures, which is a type of anonymous authentication, the service provider can authenticate a user in a way that the user to be authenticated is a member of a group but the service provider cannot know which user in the group is being authenticated right now. Using attribute-based signatures, which is also a type of anonymous authentication, the service provider can authenticate a user by knowing that the user is "(a team leader and in the accounting division) or in the sales division)" and no information beyond the fact that the user satisfies the above condition. This condition can be flexibly changed each time authentication is executed. This flexibility enables us to control how much information is disclosed to the service provider based on the needs of users and the service provider.
Our team studies highly functional and efficient anonymous authentication.
Selected Publications
- Nuttapong Attrapadung, Goichiro Hanaoka, Takahiro Matsuda, Hiraku Morita, Kazuma Ohara, Jacob C. N. Schuldt, Tadanori Teruya, Kazunari Tozawa: Oblivious Linear Group Actions and Applications. CCS 2021: 630-650
- Shuichi Katsumata, Takahiro Matsuda, Wataru Nakamura, Kazuma Ohara, Kenta Takahashi: Revisiting Fuzzy Signatures: Towards a More Risk-Free Cryptographic Authentication System based on Biometrics. CCS 2021: 2046-2065
- Toshinori Araki, Jun Furukawa, Kazuma Ohara, Benny Pinkas, Hanan Rosemarin, Hikaru Tsuchida: Secure Graph Analysis at Scale. CCS 2021: 610-629
- Reo Eriguchi, Kazuma Ohara, Shota Yamada, Koji Nuida: Non-interactive Secure Multiparty Computation for Symmetric Functions, Revisited: More Efficient Constructions and Extensions. CRYPTO (2) 2021: 305-334
- Junichiro Hayata, Jacob C. N. Schuldt, Goichiro Hanaoka, Kanta Matsuura: On Private Information Retrieval Supporting Range Queries. ESORICS (2) 2020: 674-694
- Kazuma Ohara, Keita Emura, Goichiro Hanaoka, Ai Ishida, Kazuo Ohta, Yusuke Sakai: Shortening the Libert-Peters-Yung Revocable Group Signature Scheme by Using the Random Oracle Methodology. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 102-A(9): 1101-1117 (2019)
- Kazuma Ohara, Yohei Watanabe, Mitsugu Iwamoto, Kazuo Ohta: Multi-Party Computation for Modular Exponentiation Based on Replicated Secret Sharing. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 102-A(9): 1079-1090 (2019)
- Keita Emura, Goichiro Hanaoka, Yutaka Kawai, Takahiro Matsuda, Kazuma Ohara, Kazumasa Omote, Yusuke Sakai: Group Signatures with Message-Dependent Opening: Formal Definitions and Constructions. Secur. Commun. Networks 2019: 4872403:1-4872403:36 (2019)
- Ai Ishida, Yusuke Sakai, Keita Emura, Goichiro Hanaoka, Keisuke Tanaka: Proper Usage of the Group Signature Scheme in ISO/IEC 20008-2. AsiaCCS 2019: 515-528
- Yusuke Sakai, Shuichi Katsumata, Nuttapong Attrapadung, Goichiro Hanaoka: Attribute-Based Signatures for Unbounded Languages from Standard Assumptions. ASIACRYPT (2) 2018: 493-522
- Ai Ishida, Yusuke Sakai, Keita Emura, Goichiro Hanaoka, Keisuke Tanaka: Fully Anonymous Group Signature with Verifier-Local Revocation. SCN 2018: 23-42
- Keita Emura, Goichiro Hanaoka, Koji Nuida, Go Ohtake, Takahiro Matsuda, Shota Yamada: Chosen ciphertext secure keyed-homomorphic public-key cryptosystems. Des. Codes Cryptogr. 86(8): 1623-1683 (2018)
- Yusuke Sakai, Nuttapong Attrapadung, Goichiro Hanaoka: Practical attribute-based signature schemes for circuits from bilinear map. IET Inf. Secur. 12(3): 184-193 (2018)