Cryptography with Advanced Functionality
With conventional cryptography, there is only one specific person to whom a message can be sent. However, in situations such as paid content distribution or information sharing on cloud storage, one-to-many communication is required. In these situations, using conventional cryptography for secure communication would be inefficient because it would require encryption for all users who are allowed to access the information.
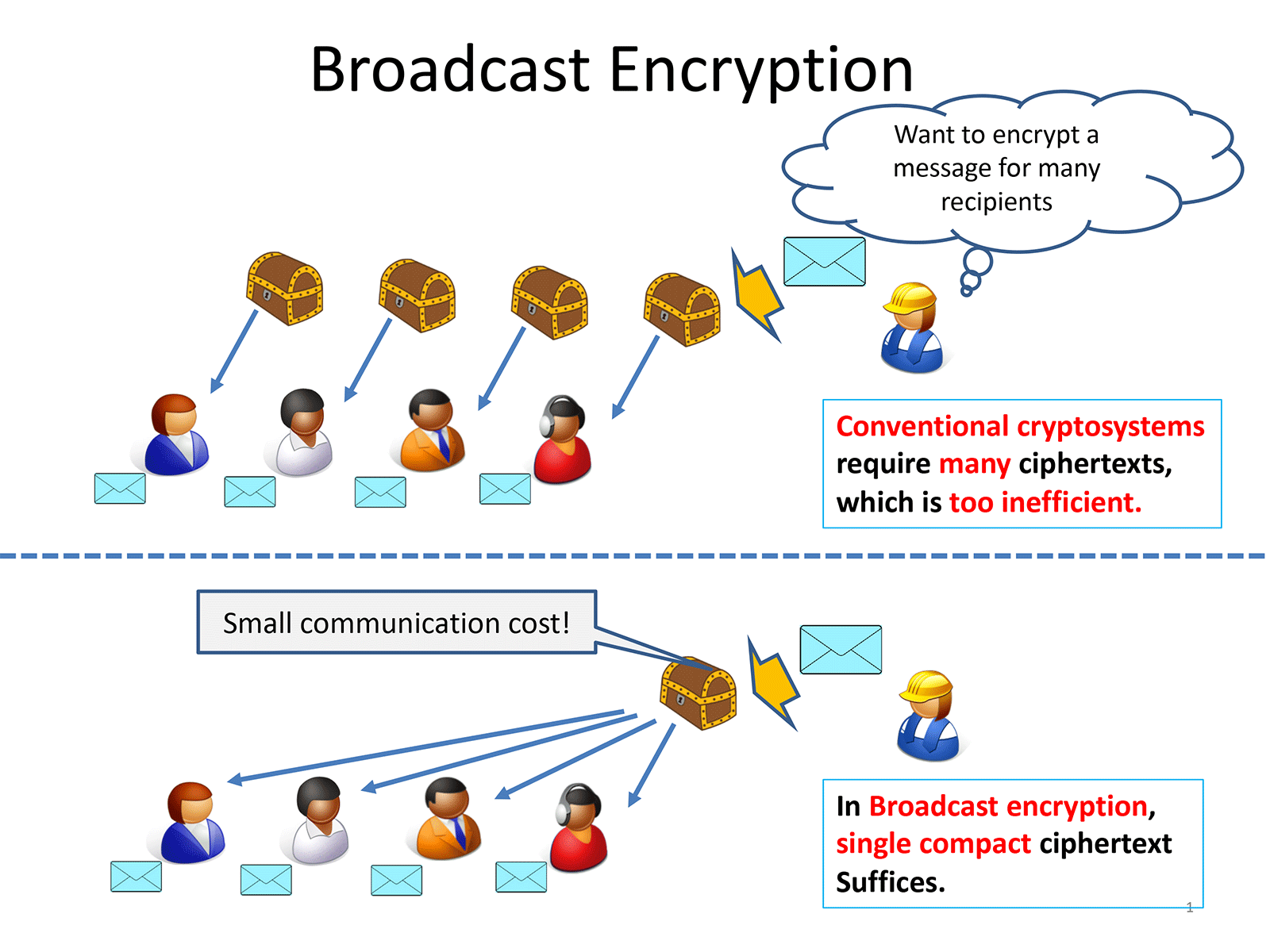
Broadcast encryption and functional encryption are known as cryptographic primitives suitable for situations where one-to-many communication is required. In situations such as pay-per-view broadcasting, it is necessary to encrypt contents and distribute it simultaneously to many users who are qualified to receive the contents. Using broadcast encryption, it is possible to securely distribute the content by creating a compact ciphertext even in the case the number of recipients is large.
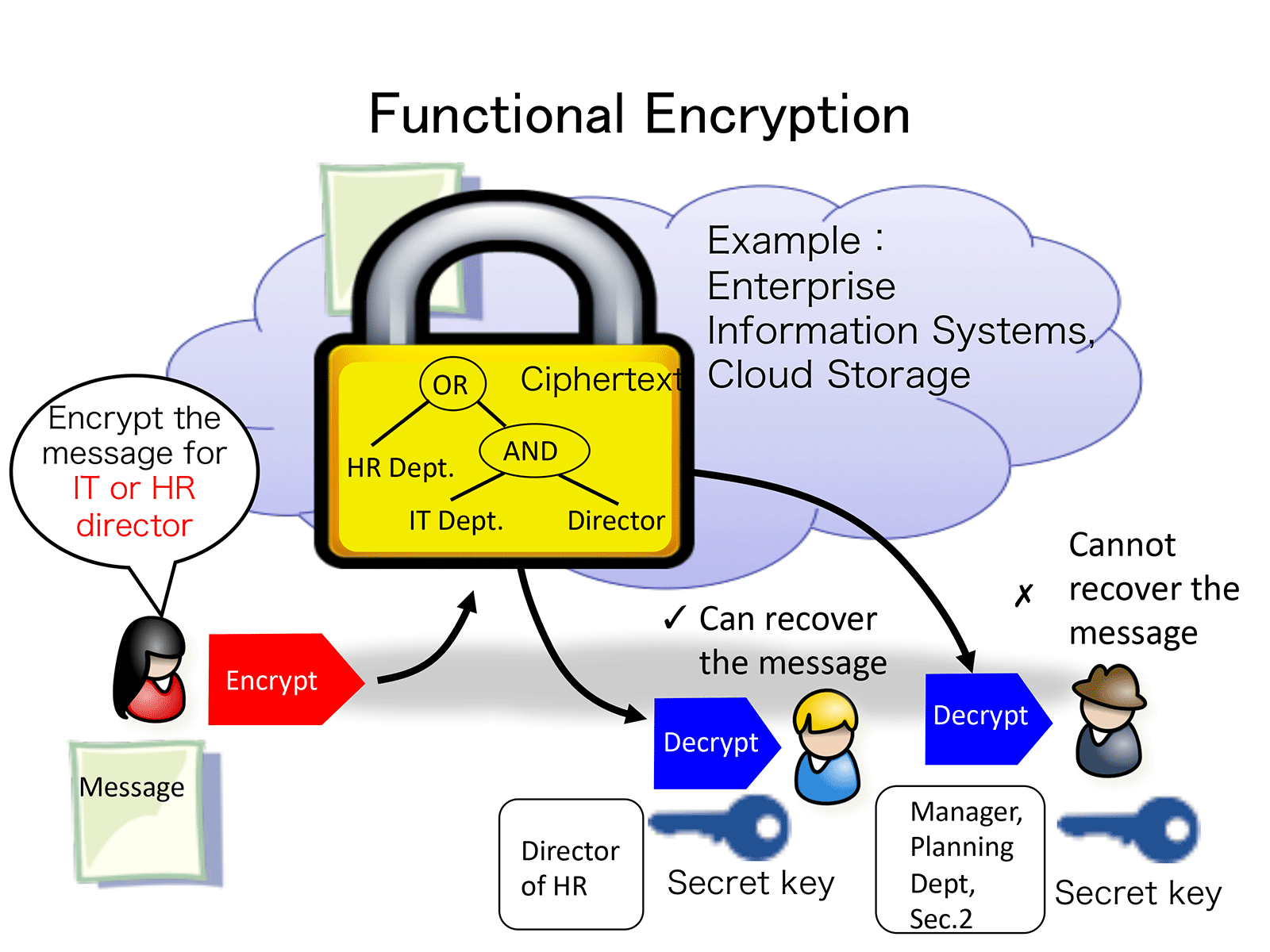
Functional encryption is useful in situations where there is a desire for controlling the access to the information according to the attributes of receivers, which may include information sharing on cloud storage. In other words, in functional encryption, the sender of a message can encrypt it in such a way that only users who satisfy certain conditions can decrypt the ciphertext and recover the information. The conditions that can be specified are expressed in Boolean formulae, for example, "(department head or higher ∨ accounting department) ∧ head office affiliation".
Our research team is conducting research to design more flexible, secure and efficient functional encryption and broadcast encryption.
Selected Publications
- Shweta Agrawal, Monosij Maitra, Narasimha Sai Vempati, Shota Yamada: Functional Encryption for Turing Machines with Dynamic Bounded Collusion from LWE. CRYPTO (4) 2021: 239-269
- Shuichi Katsumata, Ryo Nishimaki, Shota Yamada, Takashi Yamakawa: Round-Optimal Blind Signatures in the Plain Model from Classical and Quantum Standard Assumptions. EUROCRYPT (1) 2021: 404-434
- Shuichi Katsumata, Ryo Nishimaki, Shota Yamada, Takashi Yamakawa: Adaptively Secure Inner Product Encryption from LWE. ASIACRYPT (3) 2020: 375-404
- Fuyuki Kitagawa, Takahiro Matsuda, Takashi Yamakawa: NIZK from SNARG. TCC (1) 2020: 567-595
- Shweta Agrawal, Daniel Wichs, Shota Yamada: Optimal Broadcast Encryption from LWE and Pairings in the Standard Model. TCC (1) 2020: 149-178
- Shweta Agrawal, Shota Yamada: CP-ABE for Circuits (and More) in the Symmetric Key Setting. TCC (1) 2020: 117-148
- Alex Davidson, Shuichi Katsumata, Ryo Nishimaki, Shota Yamada, Takashi Yamakawa: Adaptively Secure Constrained Pseudorandom Functions in the Standard Model. CRYPTO (1) 2020: 559-589
- Takashi Yamakawa, Shota Yamada, Goichiro Hanaoka, Noboru Kunihiro: Generic hardness of inversion on ring and its relation to self-bilinear map. Theor. Comput. Sci. 820: 60-84 (2020)
- Shweta Agrawal, Shota Yamada: Optimal Broadcast Encryption from Pairings and LWE. EUROCRYPT (1) 2020: 13-43
- Keita Emura, Shuichi Katsumata, Yohei Watanabe: Identity-Based Encryption with Security Against the KGC: A Formal Model and Its Instantiation from Lattices. ESORICS (2) 2019: 113-133
- Shweta Agrawal, Monosij Maitra, Shota Yamada: Attribute Based Encryption (and more) for Nondeterministic Finite Automata from LWE. CRYPTO (2) 2019: 765-797
- Shuichi Katsumata, Shota Yamada: Group Signatures Without NIZK: From Lattices in the Standard Model. EUROCRYPT (3) 2019: 312-344
- Shuichi Katsumata, Takahiro Matsuda, Atsushi Takayasu: Lattice-Based Revocable (Hierarchical) IBE with Decryption Key Exposure Resistance. Public Key Cryptography (2) 2019: 441-471
- Nuttapong Attrapadung, Takahiro Matsuda, Ryo Nishimaki, Shota Yamada, Takashi Yamakawa: Adaptively Single-Key Secure Constrained PRFs for NC1. Public Key Cryptography (2) 2019: 223-253
- Shuichi Katsumata, Shota Yamada: Non-zero Inner Product Encryption Schemes from Various Assumptions: LWE, DDH and DCR. Public Key Cryptography (2) 2019: 158-188
- Nuttapong Attrapadung, Takahiro Matsuda, Ryo Nishimaki, Shota Yamada, Takashi Yamakawa: Constrained PRFs for NC1 in Traditional Groups. CRYPTO (2) 2018: 543-574
- Ali El Kaafarani, Shuichi Katsumata: Attribute-Based Signatures for Unbounded Circuits in the ROM and Efficient Instantiations from Lattices. Public Key Cryptography (2) 2018: 89-119